IT professionals are the people who manage and support the technology systems used in businesses and organizations. IT roles are essential because every company today relies on computers, networks, and software to run smoothly.
IT professionals work in areas like hardware support, networking, system administration, cloud services, cybersecurity, and technical support. Their technical knowledge often includes skills in operating systems (like Windows or Linux), networking basics, troubleshooting, databases, cloud platforms (AWS, Azure), cybersecurity tools, and general system management.
Preparing for an IT interview is essential because companies look for candidates who can solve technical problems and think logically while working under pressure. Interviewers frequently ask practical, scenario-based questions alongside theoretical concepts to evaluate your knowledge and real-world problem-solving skills. Proper preparation allows you to explain concepts clearly, answer confidently, and manage technical tasks during the interview.
Heer we are sharing a wide range of IT interview questions and answers, covering both freshers and experienced candidates, as well as real-life, technical, and scenario-based questions. These will help you prepare better for your next IT job interview
Table of Contents
IT Interview Questions
We have provided guides with interview questions and answers for various IT roles, so you can prepare for your desired job.
How to Prepare for IT Interview
Preparing for an IT interview can be a daunting task, but with the right approach, you can increase your chances of success. Here are some useful tips to help you get ready:
- Research the company and its culture to understand what they value in employees.
- Review common IT interview questions and prepare your answers, focusing on your technical skills.
- Practice coding challenges or technical assessments relevant to the position you’re applying for.
- Brush up on your resume and be ready to discuss your previous projects and experiences in detail.
- Prepare questions to ask the interviewer to demonstrate your interest in the role and the organization.
- Dress appropriately for the interview, aligning with the company’s dress code.
- Conduct mock interviews with friends or mentors to gain confidence in your responses.
- Arrive early to the interview to show punctuality and give yourself time to relax before it starts.
IT Interview Questions and Answers for Freshers
First, we will start with basic interview questions for freshers who are preparing for a data analyst role in the IT industry.
Que 1. As an IT staff member, how would you explain the purpose of a firewall in protecting company resources?
Cybersecurity is a key concern for any organization. Can you explain what a firewall does and why it’s critical for protecting a company’s internal systems and data from external threats?
Que 2. How do you ensure company systems are updated and secured regularly?
As part of your IT responsibilities, how would you manage system updates and security patches across company devices to ensure protection against potential vulnerabilities?
Que 3. How would you handle basic network troubleshooting in the office?
As an IT team member, how would you approach resolving common network issues like connectivity loss or slow internet speeds within a company’s local network?
Que 4. What backup solutions would you suggest for protecting company data?
Data loss prevention is critical. Could you share what backup strategies or tools you would use to regularly protect and recover company data in case of a system failure or cyberattack?
Que 5. Why is user access control important in a company environment?
Managing who can access what information is key for any business. Could you explain why setting up user access levels (such as admin, editor, viewer) is important for safeguarding company data and maintaining operational control.
Que 6. What is the difference between a compiler and an interpreter?
Answer:
- A compiler converts the whole code into machine language at once.
- An interpreter translates and executes the code line by line.
Que 7. What is a network?
Answer:
A network is a group of connected computers that share resources and information, such as LAN, WAN, or the internet.
Que 8. What is an IP address?
Answer:
An IP address is a unique identifier for a device on a network, used to send and receive data.
Que 9. What is DNS?
Answer:
DNS (Domain Name System) translates human-readable domain names like google.com into IP addresses that computers understand.
Que 10. What is the difference between HTTP and HTTPS?
Answer:
- HTTP (HyperText Transfer Protocol) is used for data transfer on the web.
- HTTPS is the secure version that encrypts the data using SSL/TLS.
Que 11. What is a database?
Answer:
A database is an organized collection of data that can be easily accessed, managed, and updated. Examples: MySQL, PostgreSQL, Oracle.
Que 12. What is SQL?
Answer:
SQL (Structured Query Language) is used to manage and query relational databases.
SELECT * FROM users WHERE age > 25;Que 13. What is normalization in databases?
Answer:
Normalization is the process of organizing data to reduce redundancy and improve data integrity across tables.
Que 14. What is the difference between primary key and foreign key?
Answer:
- A primary key uniquely identifies a record in a table.
- A foreign key links one table to another.
Que 15. What is an algorithm?
Answer:
An algorithm is a step-by-step procedure or formula to solve a specific problem using logical steps.
Que 16. What are data structures?
Answer:
Data structures are ways of organizing and storing data efficiently. Examples include arrays, lists, stacks, and trees.
Que 17. What is cloud computing?
Answer:
Cloud computing delivers computing services like storage, databases, servers, and software over the internet on-demand.
Que 18. What is version control and why is it important?
Answer:
Version control helps manage changes in code over time. Tools like Git allow multiple developers to collaborate and track revisions.
Que 19. What is cybersecurity?
Answer:
Cybersecurity involves protecting systems, networks, and data from digital attacks, unauthorized access, or data breaches.
Que 20. What is troubleshooting?
Answer:
Troubleshooting is the process of diagnosing and fixing issues in software, hardware, or systems to restore normal operation.
Que 21. What is the difference between IPv4 and IPv6?
Answer:
IPv4 is a 32-bit address protocol allowing around 4.3 billion unique addresses, whereas IPv6 is a 128-bit protocol offering trillions of unique addresses. IPv6 also provides improved routing, auto-configuration, and built-in security features, making it more suitable for the growing number of internet-connected devices.
Que 22. What is disk partitioning and why is it important?
Answer:
Disk partitioning involves dividing a physical disk into logical sections. This allows better organization of data, separation of OS from user files, and more effective disk management. It also helps in multi-boot configurations and improves system backup and recovery.
Que 23. What is DHCP and how does it work?
Answer:
DHCP (Dynamic Host Configuration Protocol) automatically assigns IP addresses to devices in a network. When a device connects, it sends a broadcast request, and the DHCP server responds with an IP address, subnet mask, gateway, and DNS information. This simplifies IP management in networks.
Que 24. What are device drivers and why are they necessary?
Answer:
Device drivers are software programs that enable the operating system to communicate with hardware components like printers, keyboards, and network cards. Without proper drivers, the OS cannot recognize or fully utilize the hardware’s capabilities.
Que 25. What is two-factor authentication (2FA)?
Answer:
2FA is a security method that requires two types of verification—something you know (like a password) and something you have (like an OTP or mobile device). It adds a layer of security, especially against stolen credentials.
Que 26. What are environment variables in an OS?
Answer:
Environment variables are dynamic values that affect how processes run on the system. They are used to store system-wide configuration settings, such as file paths, user profiles, and system behavior. For example, PATH defines directories to search for executable files.
Que 27. What is the purpose of Safe Mode in Windows?
Answer:
Safe Mode is a diagnostic startup mode in Windows that loads only essential drivers and services. It is used to troubleshoot problems like faulty drivers, incompatible software, or malware infections by providing a minimal environment.
Que 28. How does a VPN work?
Answer:
A Virtual Private Network (VPN) encrypts your internet connection and routes it through a secure server. This hides your IP address, protects sensitive data from hackers, and allows access to region-restricted content by masking location.
Que 29. What is a MAC address?
Answer:
A MAC (Media Access Control) address is a unique hardware identifier assigned to a network interface card (NIC). It is used for network communication within a local area network (LAN) and remains fixed regardless of IP address changes.
Que 30. What is the function of an operating system?
Answer:
An operating system manages hardware resources, provides a user interface, and runs applications. It handles memory allocation, process scheduling, device control, file management, and security enforcement.
Que 31. What is latency in networking?
Answer:
Latency is the delay between a request and response in network communication. It is measured in milliseconds (ms) and impacts the responsiveness of applications. High latency can result in lag, especially in video calls or online gaming.
Que 32. What are the basic steps to install an operating system?
Answer:
- Boot the computer using installation media (USB/DVD).
- Select language and keyboard preferences.
- Create or select disk partitions.
- Choose installation type (clean or upgrade).
- Complete setup and install drivers post-installation.
Que 33. What is ping and how is it used?
Answer:ping is a network diagnostic tool used to test the reachability of a host and measure the round-trip time for messages sent. It’s useful for checking network connectivity and latency between devices.
Que 34. What is a proxy server?
Answer:
A proxy server acts as an intermediary between a client and the internet. It can be used for content filtering, security, caching, and hiding the client’s IP address. Organizations use it to monitor and restrict web access.
Que 35. How do you protect a computer from malware?
Answer:
- Install and update antivirus software
- Avoid downloading from untrusted sources
- Enable firewall protection
- Keep OS and applications updated
- Regularly back up important data
Que 36. What is BIOS and what happens during POST?
Answer:
BIOS (Basic Input/Output System) is firmware that initializes hardware during system startup. POST (Power-On Self-Test) checks RAM, CPU, and storage to ensure hardware components are functional before booting the OS.
Que 37. What is remote desktop access and where is it used?
Answer:
Remote desktop access allows users to control another computer over a network. It is widely used in IT support, remote administration, and work-from-home scenarios for managing systems without physical presence.
Que 38. What is system restore in Windows?
Answer:
System Restore is a recovery tool that rolls back system files, installed apps, and settings to a previous state. It’s useful for fixing issues caused by faulty updates, driver installations, or software conflicts without affecting personal files.
Que 39. What is command prompt and how is it used?
Answer:
Command Prompt is a command-line interpreter in Windows. It allows users to execute commands to perform tasks like file operations, system configuration, and network diagnostics.
Que 40. What is port forwarding?
Answer:
Port forwarding maps an external port to an internal IP address and port, allowing external devices to access services within a private network (like a web server). It’s commonly configured on routers to support remote access.
IT Interview Questions and Answers for Experienced
We have already shared IT interview questions for entry-level roles. Now, we are sharing some senior IT interview questions and answers for experienced roles.
Que 41. How do you ensure system reliability and uptime in enterprise IT environments?
Answer:
Use redundancy, load balancing, monitoring tools (like Nagios or Zabbix), backup systems, and disaster recovery plans. Implement high availability (HA) and failover strategies to reduce downtime.
Que 42. What is the difference between virtualization and containerization?
Answer:
Virtualization uses hypervisors (like VMware or Hyper-V) to run multiple OS instances.
Containerization (like Docker) runs isolated apps using the host OS, making it more lightweight and portable.
Que 43. What tools do you use for IT infrastructure automation?
Answer:
Popular tools include:
- Ansible and Puppet for configuration management
- Terraform for infrastructure as code
- Jenkins for continuous integration
These improve consistency, speed, and reduce human error.
Que 44. How do you secure a network against external threats?
Answer:
Use firewalls, intrusion detection/prevention systems (IDS/IPS), VPNs, endpoint protection, regular patching, and enforce strong authentication protocols.
Que 45. How do you approach root cause analysis for recurring system issues?
Answer:
By collecting logs, reviewing incident history, replicating issues in staging environments, and using tools like Splunk or ELK Stack for correlation and traceability.
Que 46. How do you handle a situation where a production server goes down?
Answer:
Immediately notify stakeholders, isolate the issue, check logs and monitoring dashboards, apply fixes or rollbacks, and document the incident for future prevention.
Que 47. Explain the concept of load balancing and name a few tools used.
Answer:
Load balancing distributes traffic across multiple servers to optimize resource use and prevent overload. Tools include Nginx, HAProxy, AWS ELB, and F5.
Que 48. What is DNS propagation and how long does it usually take?
Answer:
DNS propagation is the time it takes for DNS changes (like a new IP or domain setup) to be updated across global DNS servers. It usually takes from a few minutes up to 48 hours.
Que 49. What is a zero-trust security model?
Answer:
Zero-trust assumes no user or device is trustworthy by default. Every request is verified based on identity, location, and device posture before granting access.
Que 50. How do you implement role-based access control (RBAC) in enterprise systems?
Answer:
RBAC assigns permissions to roles instead of individuals. Use group policies, directory services (like Active Directory), IAM systems, and strict auditing to enforce least privilege access.
Que 51. What are the key considerations when migrating infrastructure to the cloud?
Answer:
Evaluate costs, security, data compliance, latency, backup strategies, scalability, and vendor lock-in. Tools like AWS Migration Hub, Azure Migrate, and database replication are helpful during the process.
Que 52. How do you perform root cause analysis (RCA) after a critical system failure?
Answer:
RCA involves identifying the primary reason behind a failure to prevent recurrence. Steps include collecting system logs, reviewing recent changes or deployments, replicating the issue if possible, identifying failure points, and documenting findings. Tools like ELK Stack, Splunk, and change management logs are often used in this process.
Que 53. What are some key metrics you monitor in IT infrastructure?
Answer:
Common metrics include CPU utilization, memory usage, disk I/O, network latency, uptime, packet loss, error rates, and application response time. Monitoring tools like Zabbix, Datadog, and Prometheus are used to set alerts and dashboards for real-time visibility.
Que 54. How do you ensure compliance with data protection laws like GDPR?
Answer:
Ensure data encryption (at rest and in transit), implement access controls, conduct regular audits, anonymize or pseudonymize personal data, and maintain data retention and deletion policies. Document consent and processing policies, and ensure vendors also comply with regulations.
Que 55. What is the role of a CMDB in IT operations?
Answer:
A Configuration Management Database (CMDB) stores information about hardware, software, users, and relationships between assets. It supports change management, impact analysis, and incident resolution by offering a centralized view of the IT environment.
Que 56. How do you automate IT tasks for efficiency?
Answer:
Tasks are automated using scripts (PowerShell, Bash), configuration management tools (Ansible, Chef), CI/CD pipelines, and RPA (Robotic Process Automation). Common use cases include software deployment, system backups, user provisioning, and health checks.
Que 57. How do you handle OS-level patching for hundreds of servers?
Answer:
Use centralized tools like Microsoft WSUS, Red Hat Satellite, or Ansible for bulk patching. Create patch groups, schedule downtime, test patches in a staging environment, and monitor post-deployment logs. Rollback strategies must also be in place.
Que 58. What are your steps to harden a newly deployed Linux server?
Answer:
- Disable unused ports and services
- Set up a firewall using iptables or firewalld
- Enforce SSH key authentication
- Update all packages and apply security patches
- Install fail2ban for brute-force protection
- Configure auditing and logging
Que 59. How do you manage identity and access across hybrid IT environments?
Answer:
Use centralized IAM systems like Azure AD or Okta. Implement single sign-on (SSO), multi-factor authentication (MFA), and RBAC. Synchronize on-prem and cloud directories, monitor access logs, and automate provisioning/deprovisioning processes.
Que 60. What’s your strategy for handling zero-day vulnerabilities?
Answer:
Immediately isolate affected systems, disable risky services, apply temporary mitigations (e.g., WAF rules), monitor exploit patterns, and deploy vendor patches as soon as they are available. Communicate with security teams and vendors, and conduct impact analysis post-fix.
Que 61. How do you monitor and ensure server health in an enterprise setup?
Answer:
Server health is monitored using tools like Nagios, Zabbix, Datadog, or Prometheus. Key metrics include CPU load, memory usage, disk I/O, uptime, and network latency. Logs are centralized using tools like ELK Stack or Graylog for real-time alerts and diagnostics.
Que 62. What is infrastructure as code (IaC) and which tools do you use?
Answer:
IaC automates infrastructure provisioning using code instead of manual processes. It ensures consistency, repeatability, and version control. Common tools include:
- Terraform (cloud-agnostic)
- Ansible (configuration management)
- AWS CloudFormation
- Pulumi (supports multiple languages)
Que 63. What is patch management and how do you implement it securely?
Answer:
Patch management involves identifying, testing, and deploying updates to systems and applications to fix vulnerabilities or improve functionality. Best practices include:
- Automating with tools like WSUS, PDQ Deploy, or Ansible
- Testing in staging before production deployment
- Maintaining rollback plans and audit trails
Que 64. How do you handle configuration drift in a hybrid cloud environment?
Answer:
Configuration drift is addressed by:
- Using IaC tools like Terraform for consistent environments
- Implementing policy-as-code (e.g., using Open Policy Agent)
- Regular drift detection and reconciliation scripts
- Maintaining configuration baselines and version control
Que 65. How do you secure sensitive data at rest and in transit?
Answer:
- At rest: Use disk encryption (BitLocker, LUKS), encrypted databases, and secure access control.
- In transit: Enforce TLS/SSL, use VPNs or private links, and ensure secure API endpoints.
- Apply the principle of least privilege and rotate encryption keys regularly.
Que 66. What’s your approach to high availability in application infrastructure?
Answer:
Ensure high availability by:
- Redundancy across multiple servers and regions
- Using load balancers (e.g., HAProxy, NGINX, AWS ELB)
- Implementing failover mechanisms
- Storing data in replicated and clustered databases
- Using container orchestration like Kubernetes
Que 67. How do you respond to a DDoS attack?
Answer:
Steps include:
- Identify and filter malicious traffic using firewalls or WAFs
- Rate-limit or geo-block traffic
- Scale infrastructure dynamically (if on cloud)
- Work with ISPs or use services like Cloudflare, Akamai, or AWS Shield
Post-attack, conduct forensics, update rules, and prepare incident reports.
Que 68. How do you enforce IT policies and compliance in an organization?
Answer:
- Use Group Policy Objects (GPOs) in Windows environments
- Implement SIEM systems for monitoring
- Enforce role-based access control (RBAC)
- Conduct regular audits for compliance (e.g., ISO 27001, HIPAA)
- Use DLP tools and employee training programs
Que 69. How do you handle log management in a multi-server environment?
Answer:
Aggregate logs using centralized logging tools like:
- ELK Stack (Elasticsearch, Logstash, Kibana)
- Graylog
- Splunk
Use log rotation, retention policies, and alerting mechanisms for anomaly detection.
Que 70. What is the difference between scaling vertically and horizontally?
Answer:
| Scaling Type | Description | Pros | Cons |
|---|---|---|---|
| Vertical | Increase resources on a single server | Simple to implement | Limited by hardware |
| Horizontal | Add more servers to the pool | Scalable and resilient | More complex to manage |
Horizontal scaling is preferred for cloud-native and microservices applications.
Que 71. How do you manage configuration files across environments?
Answer:
Use:
- Templating tools like Jinja2 or Helm
- Ansible, Chef, or Puppet for environment-specific configs
- Environment variables and
.envfiles - Secrets managers (Vault, AWS Secrets Manager) for sensitive configs
Version control is maintained via Git.
Que 72. How do you automate user provisioning and deprovisioning?
Answer:
Use Identity & Access Management (IAM) tools like:
- Azure AD, Okta, JumpCloud
- SCIM protocol for automatic sync
- Integrate with HR systems for real-time updates
- Use scripts and APIs for batch operations
Que 73. What are the differences between RAID 1, 5, and 10?
Answer:
| RAID Level | Description | Pros | Cons |
|---|---|---|---|
| RAID 1 | Mirroring | High redundancy | Expensive (50% storage loss) |
| RAID 5 | Striping with parity | Balanced performance/storage | One drive failure tolerated |
| RAID 10 | Mirroring + Striping | Best performance + redundancy | Requires at least 4 drives |
Que 74. How do you investigate and resolve frequent BSOD (Blue Screen) errors?
Answer:
- Analyze minidump files using tools like WinDbg or BlueScreenView
- Check event logs in Windows Event Viewer
- Update drivers and BIOS
- Test hardware (RAM, disk)
- Perform malware scans
- Use
sfc /scannowandchkdskfor integrity checks
Que 75. How do you implement centralized software deployment?
Answer:
- Use tools like Microsoft SCCM, PDQ Deploy, or Ansible
- Package apps into MSI or EXE formats
- Use GPOs for silent installations
- Create version-controlled deployment scripts
This ensures consistency, faster rollout, and compliance.
Que 76. How do you manage mobile device security in BYOD environments?
Answer:
- Enforce MDM solutions (e.g., Intune, MobileIron)
- Use containerization to separate personal and corporate data
- Enable remote wipe, device encryption, and app whitelisting
- Implement 2FA and VPNs for secure access
Que 77. How do you perform capacity planning for enterprise systems?
Answer:
- Monitor resource usage trends using tools like Prometheus, Grafana, or Zabbix
- Forecast growth based on historical data
- Conduct load testing using JMeter or Locust
- Consider redundancy, peak traffic, and SLA requirements
Que 78. What is your strategy for change management in IT operations?
Answer:
- Maintain a change advisory board (CAB)
- Follow ITIL change management procedures
- Use ticketing systems like ServiceNow or Jira Service Management
- Perform impact analysis, rollback planning, and post-change reviews
Que 79. How do you handle shadow IT in large organizations?
Answer:
- Conduct audits to detect unauthorized tools
- Educate employees on risks and policies
- Provide sanctioned alternatives with better user experience
- Enforce network monitoring and access control policies
- Use CASB (Cloud Access Security Broker) tools to monitor SaaS usage
Que 80. How do you ensure secure software updates in enterprise environments?
Answer:
- Digitally sign update packages
- Use HTTPS and trusted repositories
- Deploy updates via centralized patching systems
- Perform staged rollouts and test in isolated environments
- Monitor update logs and rollback on failures
IT Technical Interview Questions and Answers
Que 81. What happens when you type a URL into a browser and hit enter?
Answer:
The browser checks cache or sends a DNS request, resolves the domain to an IP, establishes a TCP connection (usually HTTPS), sends an HTTP request to the server, receives the response (HTML, CSS, JS), and renders the web page on the screen.
Que 82. What is the difference between TCP and UDP?
Answer:
TCP (Transmission Control Protocol) is connection-oriented, reliable, and ensures data delivery with error checking. UDP (User Datagram Protocol) is connectionless, faster, and used when speed is preferred over reliability (like video streaming or DNS).
Que 83. How does DNS work in resolving a domain name?
Answer:
When a user enters a domain, the DNS resolver queries the root server, then the TLD server, and finally the authoritative name server to get the IP address. This address is then used to connect to the destination server.
Que 84. What is the purpose of a subnet mask?
Answer:
A subnet mask separates the IP address into network and host portions. It helps in identifying which part of the address is the network and which part refers to individual devices within the network.
Que 85. How do you troubleshoot a slow-performing application?
Answer:
Start by checking system resource usage (CPU, RAM, Disk), examine logs, test network latency, validate database queries, and monitor third-party API response times. Use tools like top, htop, or application performance monitoring (APM) tools like New Relic or Datadog.
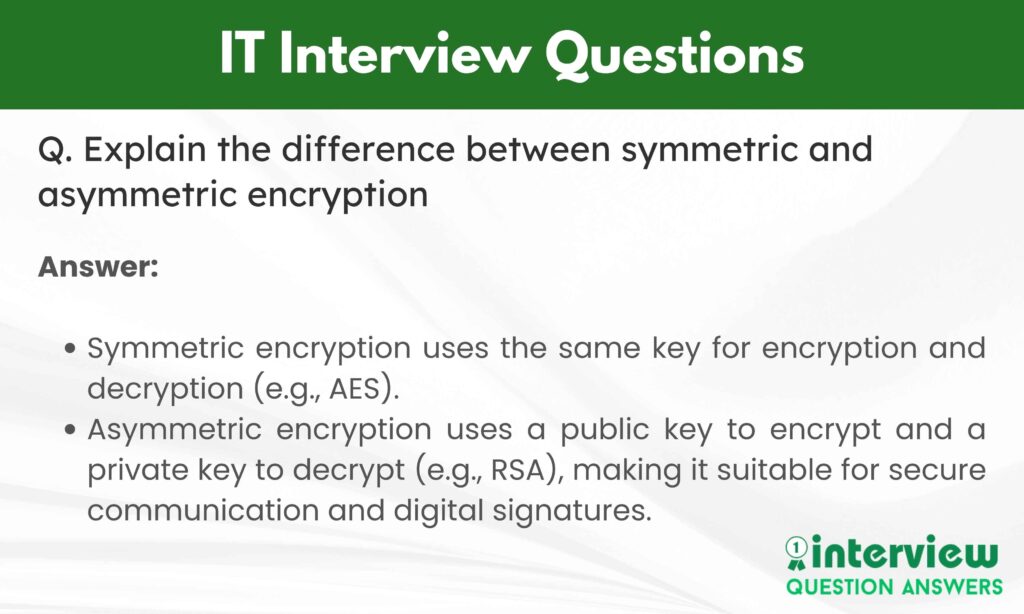
Que 86. Explain the difference between symmetric and asymmetric encryption.
Answer:
- Symmetric encryption uses the same key for encryption and decryption (e.g., AES).
- Asymmetric encryption uses a public key to encrypt and a private key to decrypt (e.g., RSA), making it suitable for secure communication and digital signatures.
Que 87. What is RAID and why is it used?
Answer:
RAID (Redundant Array of Independent Disks) is used to increase storage reliability and performance.
- RAID 0 improves speed
- RAID 1 mirrors data for redundancy
- RAID 5 offers fault tolerance and efficiency
It is commonly used in servers and storage systems.
Que 88. How do you secure a Linux server after a fresh install?
Answer:
- Update system packages
- Configure firewall rules (e.g.,
ufw,iptables) - Disable unused services and ports
- Create non-root users
- Setup SSH key authentication
- Install fail2ban or similar tools
Que 89. What is the use of cron jobs in Linux?
Answer:
Cron jobs schedule tasks to run automatically at specified times or intervals. Useful for backups, updates, reports, etc.
0 3 * * * /usr/bin/python3 /home/user/backup.pyQue 90. What is the difference between REST and SOAP APIs?
Answer:
- REST is lightweight, uses HTTP methods, and is more flexible with data formats like JSON or XML.
- SOAP is a protocol with strict standards, uses XML, and is more secure but heavier.
For more Technical focused questions, you can visit this page: Technical Interview Questions and Answers PDF
Common IT Interview Questions and Answers
Here are some common and popular basic IT interview questions that every IT candidate might face during their interview. These questions are designed for freshers or junior-level candidates and cover general concepts in IT.
Que 91. What is the role of an IP address in networking?
Answer:
An IP address uniquely identifies a device on a network. It allows communication between different devices by acting like a mailing address for digital information.
Que 92. What is the function of a router?
Answer:
A router connects multiple networks and directs data packets between them. It acts as a gateway between your local network and the internet.
Que 93. What is the difference between LAN and WAN?
Answer:
- LAN (Local Area Network) is a network within a small area like a home or office.
- WAN (Wide Area Network) connects devices over large distances, such as the internet.
Que 94. What is a firewall and why is it used?
Answer:
A firewall is a security system that monitors and controls incoming and outgoing network traffic. It blocks unauthorized access while allowing legitimate communication.
Que 95. How do you update software on a Windows system?
Answer:
Go to Settings → Windows Update → Check for Updates. This downloads and installs the latest security patches and feature updates.
Que 96. What are input and output devices? Give examples.
Answer:
- Input devices allow users to provide data (e.g., keyboard, mouse, scanner).
- Output devices display or deliver results (e.g., monitor, printer, speakers).
Que 97. What is BIOS and what does it do?
Answer:
BIOS (Basic Input Output System) is firmware that initializes hardware during the boot process and starts the operating system.
Que 98. What is software installation and why is admin permission sometimes needed?
Answer:
Software installation involves copying program files to the system and configuring settings. Admin permissions are needed to install software system-wide or modify protected system files.
Que 99. What is troubleshooting in IT?
Answer:
Troubleshooting is the process of identifying, diagnosing, and resolving hardware or software issues to restore functionality.
Que 100. What are the most common operating systems used in IT?
Answer:
The most common operating systems are:
- Windows
- Linux (Ubuntu, CentOS)
- macOS
Each has specific uses in development, servers, and desktops.
IT Interview Questions PDF
We have shared various types of questions, and we are now uploading a PDF of these questions so you can easily access the questions and answers.
FAQs: IT Interview Questions
What types of job roles are covered under IT interview questions?
Answer:
IT interview questions typically cover roles such as technical support, system administrator, network engineer, software developer, DevOps engineer, database administrator, and cybersecurity analyst. Each role demands a specific mix of technical, troubleshooting, and problem-solving skills depending on the organization’s infrastructure and needs.
What are the biggest challenges in IT job interviews?
Answer:
Challenges include solving real-time technical problems, answering scenario-based questions, handling pressure during live coding or troubleshooting rounds, and demonstrating hands-on experience with tools and systems. Interviewers also evaluate your ability to prioritize tasks, manage incidents, and communicate technical issues clearly.
How should I prepare for an IT interview?
Answer:
Start by reviewing core concepts in networking, operating systems, software, and databases. Practice solving technical issues, work on basic scripting (e.g., Python, Bash), and familiarize yourself with tools like Git, terminal commands, cloud basics, and ticketing systems like Jira or ServiceNow. Real-world scenarios and mock interviews can significantly help.
What salary can I expect in an IT role in the USA?
Answer:
Salaries vary by role and experience. Entry-level IT professionals typically earn $55,000 to $75,000 per year. Mid-level roles like system or network engineers earn around $80,000 to $110,000, while senior positions in DevOps, cloud, or cybersecurity can go above $130,000 annually in major US tech cities.
Which top companies frequently hire for IT-related roles?
Answer:
Leading companies hiring IT professionals include Google, Microsoft, Amazon, IBM, Cisco, Oracle, Apple, Dell Technologies, Infosys, and Accenture. These companies offer a wide range of roles in infrastructure, cloud services, support, security, and software development.
Are certifications important for landing IT jobs?
Answer:
Certifications can add strong value, especially for candidates without formal experience. Popular certifications include CompTIA A+, Cisco CCNA, AWS Certified Solutions Architect, Microsoft Certified Azure Administrator, and Certified Ethical Hacker (CEH). They validate your skills and make your resume more competitive.
Is communication important in IT job interviews?
Answer:
Absolutely. Even though technical skills are key, communication is equally important. Employers look for candidates who can clearly explain technical problems, collaborate with teams, and document solutions properly. Good communication ensures you can work effectively with both technical and non-technical colleagues.
Conclusion
We have already shared a comprehensive collection of questions and answers tailored for various IT roles, catering to individuals from freshers to experienced professionals.
In addition to this valuable resource, we have also provided a PDF that consolidates these questions and answers, making it easier for candidates to prepare for their data analyst interviews effectively.







